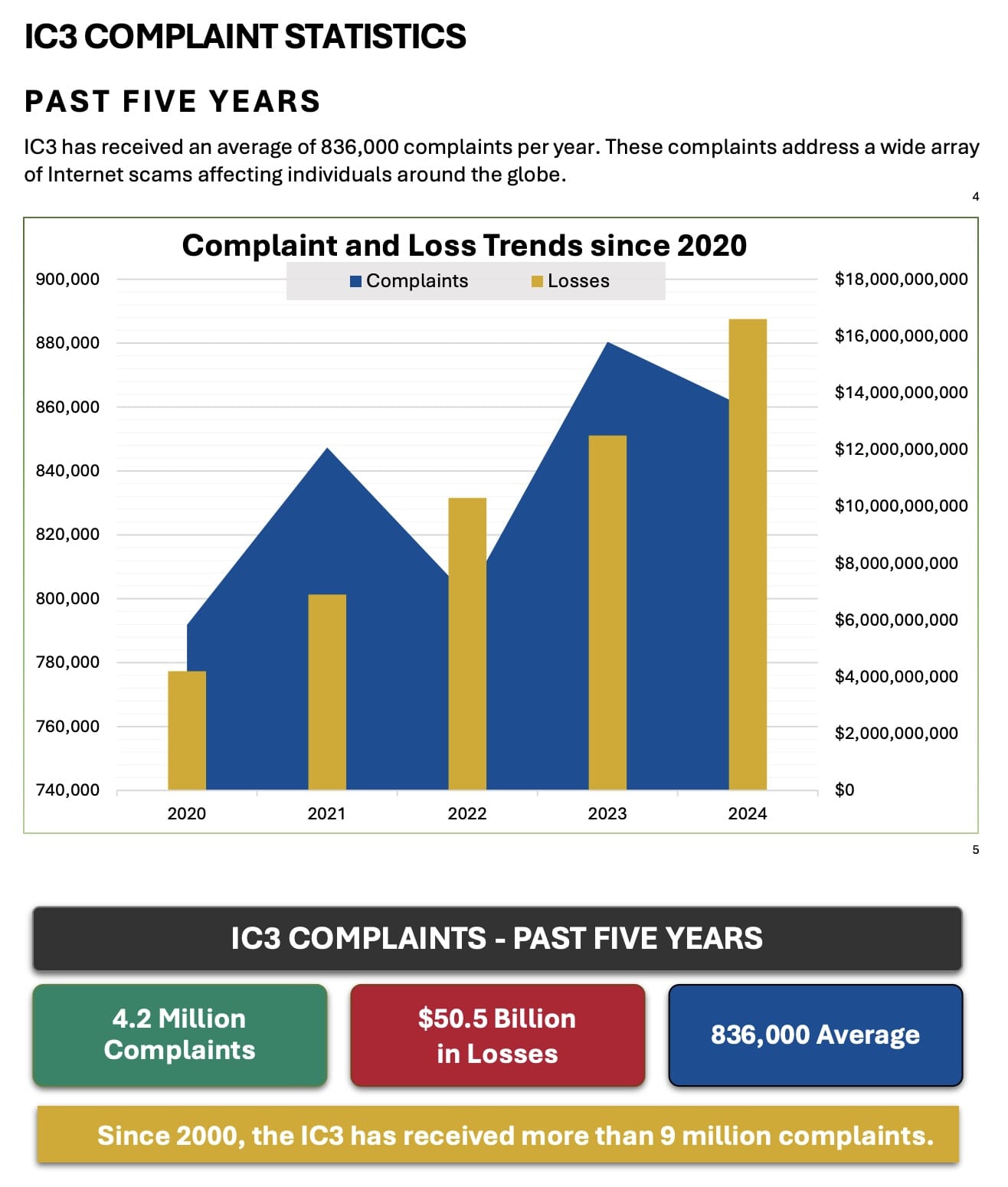
Scams aren’t what they used to be. These days, AI can write perfect emails, mimic voices, and even fake a video call so well you’d swear you were talking to the real person. The problem is, the timing of a scam can be just right when you’re distracted, busy, or looking for exactly what they’re offering. That’s when even the most careful person can get caught.
My guest, Ritesh Kotak, knows this world inside and out. He’s a cybersecurity analyst, an Ontario lawyer, and a tech innovator who’s worked with Fortune 500 companies and served in policing, where he helped start one of Canada’s first municipal cybercrime units. He’s got a BBA, MBA, and JD, all focused on privacy, cybercrime, and the way emerging tech impacts everyday life.
In our conversation, Ritesh explains how criminals are using AI as a weapon, how it can also be a shield, and why simple, low-tech steps, like having a secret phrase with family or confirming a request through a different channel, are still some of the best defenses. He even shares a close call he had himself, which is a good reminder that nobody’s immune when scams are this convincing.
“When you combine breached data from multiple sources, it paints a disturbingly complete picture of someone’s life, and scammers use that to build trust before they strike.” - Ritesh Kotak Share on XShow Notes:
- [00:50] Ritesh shares his background as a lawyer helping clients navigate AI, tech, and cybercrime.
- [01:18] His fascination with technology began at age three after taking apart his father’s computer.
- [03:59] In policing, Ritesh saw early signs of cybercrime blending with physical crime.
- [06:55] He demonstrates cybersecurity risks by live hacking a police chief, leading to the creation of a cybercrime unit.
- [09:16] A near-miss phishing scam involving discounted amusement park tickets highlights how timing plays a role.
- [15:14] Spoofed calls and evolving scam tactics make detection harder despite telecom safeguards.
- [17:09] Ritesh explains AI as both a sword for criminals and a shield for protection.
- [20:00] Generative AI enables flawless phishing emails, fake websites, and realistic deepfake audio and video.
- [28:00] Simple defenses like secret phrases and multi-channel verification can stop many scams.
- [31:45] Reporting scams to police can help investigations and sometimes recover funds.
- [33:17] Ritesh advocates for centralized fraud response centers to improve victim support.
- [36:45] Calling a lawyer can help victims navigate legal and civil remedies.
- [38:05] Final advice: pause, verify, and use low-tech habits to prevent high-tech crime.
Thanks for joining us on Easy Prey. Be sure to subscribe to our podcast on iTunes and leave a nice review.
Links and Resources:
- Podcast Web Page
- Facebook Page
- whatismyipaddress.com
- Easy Prey on Instagram
- Easy Prey on Twitter
- Easy Prey on LinkedIn
- Easy Prey on YouTube
- Easy Prey on Pinterest
- Ritesh Kotak
- Ritesh Kotak – LinkedIn
Transcript:
Ritesh, thank you so much for coming on the Easy Prey Podcast today.
Thank you so much for having me.
Can you give the audience and myself a little bit of background about who you are and what you do?
My profession, I'm a lawyer. I'm licensed in Ontario, Canada, and my role is I help clients navigate the AI tech cyber privacy world. We hear about breaches all the time, and it can be very scary. We hear about new technology and that can be very scary, and mainly with organizations, but also individuals. I help them navigate the space. I help victims of fraud as well. I actually started my career in policing. I was with two police services in Canada in multiple roles, but mainly around technology—computer crimes, cyber crimes, research and innovation, helping develop cyber crimes units as well before I decided to transition to big tech and then decided to become a lawyer. All that being said, my fascination with technology actually started when I was three years old when my father came home with a Pentium 486 running Windows 3.1.
I'm dating myself a little bit. He came home with this beautiful machine, and I remember taking it apart and I couldn't put it back together. We didn't have lots of money at the time. These things were very expensive. He needed it for his business he was in—he had a grocery store, and he goes, I, he wanted to do accounting with it. I just broke his machine, essentially. I took it apart and I could have put it back together, but instead of getting upset at me he actually said, “That's OK.” I remember going to one of the only computer stores at the time—now we kind of take it for granted. We can just walk into these big box stores and sometimes cheaper just to buy a new computer.
Not at that time, you had to get it repaired. You had to get it fixed. I remember this individual putting the computer together, and I was like, “Wow, this is great.” Brought it back home. I took it apart again but now I could put back 25% of it, and by the third time, I was actually building computers. That's where my fascination with this began. It's this magical box and this—all those modem sounds.
Yeah.
The gateway to the world. You know, ask [inaudible 00:03:09]. I think we all remember that Yahoo. This was back in the day AOL, right, was around, and that's my fascination with technology. I always thought I was going to get into the—help my parents and get into business and my undergrad and business, but ended up deciding to serve my community and join policing only to be roped back into the tech side of things. And I've just stuck through it. It's ingrained in me. You think tech lawyer, you think cyber crime. But it started when I was three with a Pentium 486 running Windows 3.1.
Nice. I remember those days. And I was one of those guys in the shop trying to put computers back together when people's kids took them apart for them. When you were in law enforcement, was the division that you worked for, was that your choice or was that someone made that decision for you?
Put it this way, they really didn't know what to do with me, and I really couldn't fit into an org chart that time. I got hired in 2010, and at that time, technology was really coming to the forefront in its use.
We thought about the good, but there was also the bad and the evil that was associated with it. We started seeing fraud. We started seeing organized crime leveraging technology. It became this area of, “How is this going to impact everyday policing?” I presented this concept, and the concept was, “Look, crime is no longer going to be physical. It's also going to be virtual as well, but it's going to be co-mingled. In other words, it's not the physical world, it's not the virtual world.”
It's this new convergent world between the two. It needs to be as competent in the physical world dealing with victims as you are in the virtual world. We saw that—we saw people being harassed online even before these AI deep fakes and all that stuff, right? We saw fake email addresses that were being created. Obviously there was no verification. Email addresses were free, but it was having a real impact on an individual's life. We started seeing dating profiles—that was a big issue. Online forums and classified ads that were fraudulent in nature. You had to be able to preserve data. You had to be able to put attributes to put someone behind a computer.
There were jurisdictional issues that were emerging as well. Servers located all over the world with victims all over the world with accused individuals all over the world using very sophisticated tools. How do you navigate that space? I was in the right place at the right time, and there's a story that the former police chief does talk about publicly—I know I can share it. Just to put into perspective, I think I was 24 years old. I'm really young. I get a meeting with the police chief of a major police service, and all the deputy chiefs were around. I was clearly the youngest guy in the room. I know we had the IT director there as well. And I have a meeting with the chief, and I turned to him, and I was like, “Chief, do you believe that cybersecurity and cyber crime is an issue? Can we as a police service be vulnerable?”
And he says, “I don't think so.” And I was like, “Well, let me demonstrate it, Chief.” And I live-hacked him. I was able to get access to his device. I knew there was a vulnerability that had been patched. And as I'm sure some of your listeners know, if you have those vulnerabilities, the vulnerabilities can be exploited. And that's exactly what we did in a safe environment. And it was to demonstrate a point. And that point was, “Chief, we got to get this right because this is going to impact our core function.” And by the way, before the meeting, the deputy chiefs actually took me aside, and there were two of them or three of them, or two of them, but I know two specifically just towering over me.
I'm not a big guy. They're towering over me. And they look at me like, “You got a meeting with the chief here? Don't do anything stupid like hacking.” Obviously he went in and hacked him. I did the complete, complete opposite. But instead of disciplining me, he understood that this was a risk, but also an opportunity. And what we ended up doing was, that ended up creating the first municipal cyber crimes, one of the first municipal cyber crimes unit in the country and within Canada. And it also got me on the circuit. I was at major city chiefs of police. I was at the FBI National Academy Institute. I got to travel the world talking about computer crime, cyber crime, and kind of what we have to do today to deal with the issues of tomorrow. To a long-winded way of answering that question around the fact that nobody really knew what to do, it was kind of right place, right time, and it was the formula and the formula being, it's 90% opportunity, or 90% preparation, 8% opportunity with 2% luck in it. That's just everything just lined up.
That's great. That's a great story. You were talking a little bit about hacking the chief and showing that any, in some sense, that anybody is vulnerable and that if the police department's vulnerable, then my gosh, what's the regular public going to be like? And one of the questions that I'd love to ask my guests, particularly those in cybersecurity, counter fraud, counter scam is have you ever been a victim of a cyber crime, a scam, or a fraud, and do you have a story to tell about that?
I've had family members that were victims, people that I deal with on a daily basis. But me personally, I've gotten pretty close, like really, really close. It was just a combination of multiple factors lining up. I love amusement parks but those tickets are expensive, right? You're spending hundreds of dollars to get tickets. And let's not even mention the cost of water and food while you're there. You're always looking to, “Hey, if I can get a discount code and save a few dollars, great.” And I called one of my buddies up and I was like, “Hey, you have a discount code for this. Can I borrow it? Can I save a few dollars? I can put that money towards, I don't know, like $500 for parking or whatever it was going to cost me.” “Absolutely, I'll send it over.” And I get an email from him and it's a link. I click on the link, and I literally start filling it out because I figured the link showed the tickets heavily discounted. But obviously it wanted my information and then credit card information. And as I started typing my, about to type in my credit card information, I noticed that there is no lock. When you look on the web browser, if you're putting in your personal information, it's H-T-T-P-S, you have the pad lock, it means it's encrypted and secured. Well, that wasn't there. And I was like, “Is this legitimate?” Sometimes high-tech crime, low-tech solutions. I picked up the phone. I just called him. I was like, “Hey, man. Are you sure this is the right link?” And he goes, “What link?”
Oh, wow.
And he goes, “I never sent you a link.” And it just so happens, what are the odds? Like his account was hacked, and obviously this is the time when everyone's going to amusement parks. And somebody used his account, which happens all the time, right, with these hacked accounts to spam the address book. I happened to be in his address book. I just happened to be looking for those tickets. What are the odds? Pretty high. Actually, pretty good, given we're seeing more and more of this. But I came close.
There is a stigma attached to it. There's a lot of people—“I don't want to talk about this. I don't want to report it.” There's a sense of, “I'm embarrassed. How could I fall for this?”-Ritesh Kotak Share on XLuckily, I didn't put in my information. But if it can happen to me, and it can happen to absolutely anybody, and I've dealt with other lawyers, I've dealt with really smart people, computer scientists as well, that have called me and said, “Ritesh….” I've been police officers that are in the fraud department as well, that have called me and said, “Hey, I accidentally did this, or can you help me sort out this mess that it's now created?” There is a stigma attached to it. There's a lot of people—“I don't want to talk about this. I don't want to report it.” There's a sense of, “I'm embarrassed. How could I fall for this?”
These are professionals. These are professional scammers. It's continuously evolving. There's absolutely zero shame in it. I think collectively as a society, we definitely need to de-stigmatize this whole area that you are a victim of something that is extremely sophisticated. It doesn't mean that you're any less intelligent.
I think collectively as a society, we definitely need to de-stigmatize this whole area that you are a victim of something that is extremely sophisticated. It doesn't mean that you're any less intelligent. -Ritesh Kotak Share on XYeah, pretty much anybody is at risk, but I think we're all at risk, and we're definitely all being targeted by the scammers. It's a story I keep hearing over and over and over again about it just being the right offer, the right context of the scam at just the right time, that if it were a month earlier or a month later, you would have known it was a scam and just deleted it or moved on, or called your friend, your buddy and said, “Hey, your email's been hacked.” But just at that right moment, it was exactly what you were expecting. And so, hey, let's click on it and start going down this road.
There's information that we hear about breaches all the time. Financial institutions, social media platforms, you name it. Retail stores, online marketplaces that are continuously being breached and hacked. They're not just looking for your credentials when they do the data dump, they're dumping and exporting as much information as possible. When you start taking information from a particular marketplace, information from a financial institution, information from an email, a server that might have been compromised, or a CRM system of an organization, and you compile it and you aggregate it, it paints a pretty intrusive picture on someone, which hackers and fraudsters purchase, right? They will purchase this information because it's gold, right? It really is gold. And now someone's going to call you up and say, “Hey, Ritesh. About this purchase you made at this location on this day.” And they will use that information to add an element of trust, to help you verify and validate, I spent $7 and 84 cents, you know, at this particular location. “OK, yeah. Tell me. You seem legitimate. OK, let's have a further conversation.” And you're in hook, line, sinker.
Yeah, I've heard more consistently stories from people I know of getting phone calls from the brand that their bank is or someone claiming to be from their bank with the caller ID being the toll-free number for their bank. I get a phone call, it's like, “Hey, this is So and So from Bank of America.” And I'm like, “Well, I don't have a Bank of America account,” I'm going to hang up right away. Or, “Hey this is Bob from your bank.” I'm like, “Why would he call himself ‘your bank?’” More frequently, my friends are getting calls from scammers actually having the right bank.
You mentioned something interesting there, right? And that's the phone number that actually comes up, that shows the bank's phone number and what we call spoofing technology, right? Being able to call someone or email someone with a number that isn't yours. Now, technology is getting better, making it more difficult to spoof. I can speak about Canada as well, that from an infrastructure level, they've made it even more difficult to engage in spoof calls, these devices and telcos, now telecommunication companies are implementing systems as well. The call is actually stopped before it comes to you or some of you might have got a call and it says “likely spam.” Like, there's big letters now.
It is technology companies that are trying to fight back, but it's like whack-a-mole, right? And you're always playing cat. You're always playing cat-and-mouse here. Tools get developed based on the type of scams that are discovered. And you figure out how to patch one scam, you hit that one, you whack one of the moles, right? But there's two more that pop up, and you need to figure out, “OK, now this is how it's evolved. This is how the scam has morphed.” And now you have to figure out a new way of dealing with that. And technology is just making it that much more difficult. We’ve got emerging tech. We’ve got, and obviously the big one being artificial intelligence.
How are you seeing artificial intelligence starting to interact with fraud these days?
When I think of AI and scams and frauds, I think there's two conversations in my world and the easiest way to break it down is AI as a sword. It’s being weaponized against individuals and then all, and then the other hat is AI as a shield being used to protect individuals from fraud. And I think the shield one is easier to talk about right off the bat. Banks are banks, organizations implementing new technologies to discover anomalies. Being able to look at inauthentic behavior, shut down accounts, that's the things that we think about. Sometimes maybe you called your bank or an organization and they verify you based on your voice.
Yep.
Biometric verification of some sort or some level of multi-factor authentication that leverages artificial intelligence. But that being said, let's wear the other hat now and let's look at the opposite side of the coin, which is a sword. And from the sword perspective, we are seeing some very interesting uses.
The most obvious one is, are those email scams? Yeah. We will get to voice in a second, but those email scams, when I used to get these phishing emails, I knew they were phishing emails. Why? They had spelling errors, the links were broken, the images looked off, the colors were off. Now with generative AI, it is extremely simple to go in and have a draft, an email for you to do something figuring out what the color schemes are, generating images, personalizing a letter based on, or an email based on the information that may be available about a particular individual.
It seems customized and grammatically correct, no spelling errors. All the links work, and it just makes it. And then you add to that spoofing technology and other types of technology, it makes it even more difficult to decipher fact from fiction. That’s how AI is clearly being used from a phishing standpoint. Stuff that's written, and even when you clicked on those links, I remember going to the website and the website looked completely off. With a few prompts, you can make a website in seconds that mirrors another website. You literally say, “Create a website identical to this, just change the logo.” Then you just go in and you change the logo to whichever company or organization you want. You purchase a domain and people are getting really, really clever, right?
If there's a W in the domain, they will put two V’s. Yeah, right? I like when you're quickly looking at it, it looks like W, but instead it's two V’s. That's the type of stuff that we're seeing. That's only being made possible because of generative AI. The fact that it only takes seconds to do something that would normally take days to do with clear and glaring issues. There's the next generation of this is audio video. From an audio side, grandparents scams are definitely on the rise. That's when the grandchild calls and says, “Grandma, grandpa, I've been arrested,” or, “I'm in trouble, and can you transfer me some money?” And the voice is identical.
All that info, it seems that everything is on par. The phone number might be pretty close. And the reason for that is all you need is just a sample of someone's voice and you're able to recreate someone's voice, making that much more difficult. Then on the extreme, now we're getting into these deep fakes and videos. There have been documented situations where individuals have been on Zoom calls or team calls or whatever platform they like to use, and there's 10 people on that call, and they're telling this poor financial assistant or administrator to change the payment, the banking information for a particular company, and having a full-on discussion. Well, out of the 10 people, you only have one real human being. The other nine are deep fakes.
There's been some documented cases of that. You're literally having conversations with bots and there is no legal requirement right now to identify if something is AI-generated. There are labels on social media sites. There are certain labels that certain applications put out. There's watermarks as well that it's fake, but not everyone is playing by the rules and there isn't a global playbook on what to do. As the technology gets better, as processing gets cheaper, which is kind of the arms race that we're seeing now with super intelligence and just this whole AI world, it's going to become even more difficult to decipher fact from fiction.
Yeah. It used to be, when I started the podcast about five years ago, the conventional wisdom was jump on a FaceTime call, jump on a Zoom call with somebody. If there's any question as to whether they're real or not, you jump onto those calls. And if they, “Oh, I'm at the airport and it's really grainy, or “Oh, I have bad internet connection.” There's always an excuse of why they can't do it. That was your red flag to, OK, be really careful about this person now with the real-time video AI. Unfortunately, it's not good. It's not valid advice anymore. If you are a consumer and you're jumping on a Zoom call with somebody, how do you even verify if they're AI or not? Is there a way?
I don't think so. Even if we come up with a way, people just figure out a way to circumvent it, right? I think a lot of high-tech crime, low-tech solutions. One thing with people that I do know, that I am having conversations with especially—look, my friends, my family, there may be a legitimate need that they need funds transferred. I've had those calls in the middle of the night. You know, I'm not going to leave my friends stranded or my family stranded if they need something. There have been legitimate situations. What we did as a family, and what I do with some of my most trusted friends is we just go low-tech. We have a secret phrase.
What we did as a family, and what I do with some of my most trusted friends is we just go low-tech. We have a secret phrase. If you don't use that phrase, I won't believe that it's you. -Ritesh Kotak Share on XYeah.
If you don't use that phrase, I won't believe that it's you. Sometimes, you just hang up and you call the number that you actually have on your phone, right? Instead of it being a FaceTime or a WhatsApp message or whatever, I just pick up the phone and call and be like, “Is this you? Did you send me this email? Are you the one,” you know? Especially if they're asking for something.
Yeah.
A lot of these fraudsters, they'll try to keep you on the device, on that phone, without hanging up. That kind of restarts everything for them. There's that sense of urgency. There's pressure tactics that are used. There’s aggression. They want to keep you on that. They don't want the call to end. Just hit that pause button, take a deep breath, have that secret phrase. That's kind of what I do. But other than that, like, is there a way, like are there apps out there that can detect? Yeah, there are apps out there, see it more with texts.
You're starting to see that with images. We don't really see that with video. But clearly with images, the metadata behind those images, which can be manipulated as well. But with text, which can be manipulated as well. But it's better than nothing.
It’s all you have to verify everything. Anything that's unexpected, you have to verify. It's the business practice that I put into place years ago, is that if anyone that I'm dealing with wants to change their payment method, if they email me, I call them. If they call me, then I email them. I always choose a different method of communication to confirm the message. Just because you could fake voices, you could fake emails, but usually it's a little more complicated to both get the person's phone number and their email at the same time.
Yeah. And there's been documented cases of major organizations that have fallen victim to this, including municipalities, governments, cities. There’s, I believe, there's a lawsuit going on right now in a city in Ontario. They're saying, “We paid the bill.” Well, they paid the bill but they paid it to a fraudulent account because somebody called and now this company's out of money. The taxpayers are out of money. It does insurance actually kick in. A lot of people think that insurance would kick in. The example I like to give people is that you might have vehicle insurance. Again, depending on your jurisdiction and kind of the rules and laws around it. But if you're impaired or if you're driving like a maniac and you're involved in something, you know insurance may deny your claim.
It is the same thing with the cyber insurances. Did you have the right protect mechanisms in place? Were people trained? Were your stuff updated? It's not like they're just going to pay out. The model's pretty simple, right? Collect the high premiums and pay out the least amount, right? Like, that's the model. You have insurance, that means you're going to have a safety net. It is there; I do recommend it. But you also have to do your due diligence. A lot of people don't.
Coming from the perspective of a victim reporting stuff, where should they report it and what are some of the challenges that might be faced with the reporting, and then if it even results in an investigation, some of the challenges with the investigation?
The main role of law enforcement or policing organizations is to police, right? It's not really to make the victim whole, it is to figure out who's behind committing the crimes. And if they're able to seize any assets, you may get some sort of restitution. You may be able to collect some funds, but it is extremely rare. However, that being said, I always recommend there's multiple ways of doing this. The first one is, think of it from a criminal perspective. And the second one, think of it from a civil perspective. From the criminal perspective, report it to local law enforcement. There's multiple reasons for that. Number one, you may have a piece of the puzzle that they're looking for. You're definitely not the only person that's been victimized by this particular group. And sometimes it's a phone number, sometimes it's an email address.
Sometimes they forgot to use a VPN and you're able to get their IP address through the metadata, or what we call the header around the email. We don't know and you don't know. Report it to your local police service and then they will—there’s federal agencies in just about every country that deal with cyber crime, or fraud, or anti-fraud. Depending on your jurisdiction that the report may be escalated to, they might have it for statistical purposes, or there might be a major takedown that's happened before where there was a takedown in Europe, funds were seized. They were Canadian victims. And they were able to get back some funds only because they reported the incident.
I'd be reporting the incident clearly for an organization. Seek legal counsel before you do anything, but you want to report it. And then the second is from a civil component. And that is, how do we get my money back? It really depends if the scam involves a credit card. If you made a purchase on a credit card, if you made any type of transfer, there may be a chargeback process or dispute process that you can leverage that you can use.
I'd be calling the financial institution right away. Sometimes it might be 24 hours before you've discovered that you're a victim of a particular scam. Sometimes there's holds on accounts. Even though the money has left her account, it hasn't left the bank or it hasn't been deposited and could actually be retraced. Right away, you want to contact, the bank. First, I'd be actually contacting the bank, or the financial institution, or the organization to see.
Usually, these things are financially motivated. It's not around theft of data, it's more around theft of funds. As quickly as you can try to get the money stopped and then obviously reporting it to your local policing organization. It's a crime in just about every jurisdiction. It's a crime to commit a fraud within, and with some, with very severe consequences. I'd be reporting it. So those are kind of the two ways. And then there's very, very specific things depending on the jurisdiction. There might be maybe you get a response back from a bank, that was, “Sorry, too bad. We're not going to do anything about it.” Then there might be stuff that's prescribed in law when it comes to appealing it.
There may be an ombudsperson or somebody who you can appeal that decision to. There may be the civil court system as well. You want to talk to somebody competent who understands the criminal components, but also understands the civil components who's dealt with these things before because they're continuously changing. I've dealt with situations that are just so complicated. You see this a lot with the crypto scams, right? Where you’ve have hot wallets and cold wallets. You’ve got exchanges in different countries. At that point, you want to report it to those platforms as well.
They may be able to do what's called a preservation request. They preserve information and accounts. They may be able to seize accounts, pending court orders. But once that money's out, it is out. The faster you act, the faster you're able to get in contact with customer service or a fraud department. The higher the probability, which is low to begin with, but you want to increase your chances that you might be able to get your funds back.
I know of a story where someone had been a victim of a scam and they had ended up wiring money to an incorrect account. They called their bank and their bank was like, “Oh, sorry, the money's already gone. There's not a whole lot we can do.” It's effectively the equivalent of you handed somebody the cash and he was relatively clever and went, “You know what? I'm going to call the receiving bank.” And he was able to get a hold of the fraud department at the receiving bank and get them to freeze the funds before they were taken out of the account.
He was really lucky that his bank wasn't helpful, but the receiving bank was, “Yeah, we'll look at it. We'll hold the account.” And they got back to him within like an hour or two. They're like, “Yeah, we see what appear to be fraudulent transactions with that account, so we have frozen it and we're going to reverse the transaction for you.”
You bring up a great point there, right? That was a fantastic outcome. But why did he have to call the receiving, right? I think that's the moral of the story here or, like, the big question mark for me is why, right? That's why I've been a big advocate for having centers of excellence or some sort of hub where you have representatives of the government of these fraud investigators. You have the police services there as well, you're calling one person and you're dealing with everything.
It's one thing to go and be on hold and trying to deal with a bank versus if we're all in the same room, or we can just turn and say, “Hey, this bank account. There's a wire coming in. The money hasn't been taken out.” Now can you just freeze it and boom, it's frozen. We need to rethink our approach to dealing with these crimes. The example I give is we have 21st century crimes, but we're using 20th century frameworks. We really need to rethink, like, how do we put the victim front and center? The victim literally gets re-victimized by these processors.
We need to rethink our approach to dealing with these crimes. The example I give is we have 21st century crimes, but we're using 20th century frameworks. We really need to rethink, like, how do we put the victim front and center?… Share on XYeah. It's almost like what you see in the series FBI, the TV series. They've got everybody in their operations center together. “Hey, DEA. What do you see about this? Hey, local police department. What do you have?” It'd be nice to see that in dealing with scams.
We deal with it in the physical world, right? We’ve got operation centers, real-time crime centers, you know, deconfliction centers, you name it. We have all these centers, all these war rooms, essentially. They are well-documented. They exist. Banks have their own as well. Airlines have their own as well. Maybe we need to make this more specific to victimization instead of just profits. How do we have all these people so we can be more effective, be more efficient, but also in this case, how can we have something that will help make victims whole and bring these people that are committing these offenses to justice?
Yeah. From a lawyer's perspective, is there much that could be done after the fact? You're talking civilly, but is there much that, you know, calling a lawyer can help with?
I do recommend calling a lawyer, especially if you're not getting the—if sometimes it takes a lawyer just to even get a response from certain organizations. They just don't respond. But once they get a letter from a lawyer, they seem to take it more seriously. It should not be the case. That should 100% not be the case. Contact a lawyer. They will help you navigate the system. There may be some civil remedies that are available as well against organizations, especially if they were negligent in putting any safeguards in place from something occurring in the first place. Every situation is different, but I do recommend to contact a legal professional within your jurisdiction who specializes in these areas to see what your rights are and how to make yourself whole.
Awesome. As we're wrapping up here, do you have any parting advice for our listeners today?
It's not how do we prevent particular types of frauds and particular types of crimes, it's how do we ensure that we have the right skill sets to deal with these frauds as they continue to emerge? -Ritesh Kotak Share on XI think just to sum up, if there's one takeaway here, it is the crime. These frauds and these cyber crimes are just going to keep evolving. They're going to get even more sophisticated. It's not how do we prevent particular types of frauds and particular types of crimes, it's how do we ensure that we have the right skill sets to deal with these frauds as they continue to emerge? The best advice to tell people is high-tech crime, low-tech solutions. Hit that pause button, take a breath, ask a friend. If you're unsure if something is legit or not, pick up the phone, call the sender of that message. Especially if they're asking for sensitive information or there's links, you know, validate, verify. It's a lot of these, again, high-tech crime, low-tech solutions. But if you do become victimized, putting the toothpaste back in the tube, it's just not possible. Preventing that from happening in the first place is much better than finding a cure.
The best advice to tell people is high-tech crime, low-tech solutions. Hit that pause button, take a breath, ask a friend. If you're unsure if something is legit or not, pick up the phone, call the sender of that message. -Ritesh… Share on XAwesome. If people want to be able to connect with you online, where can they find you?
riteshkotak.com. Ritesh Kotak on Twitter, and Ritesh Kotak on LinkedIn.
That's super easy. Thank you so much for your time today.
Thank you so much for having me.